Exploiting interference for physical layer security in 5G networks (CI-PHY)

6 July 2018
Exploiting constructive interference to enable Physical Layer Security
Funder EPSRC
Amount 1 100 000 GBP (total)
Project website http://gtr.ukri.org
Description
Security and privacy have become a paramount concern in modern ICT, as threats from cybercrime are soaring. This year's global economic crime survey conducted by PwC reported that cybercrime has jumped from 4th to 2nd place among the most-reported types of economic crime.
The severity of threat on the business, financial, infrastructure and other UK sectors makes all facets of security and risk management pertinent, and their importance cannot be overstated.
Physical layer security (PS) provides an extra layer of security on top of the traditional cryptographic measures. It obstructs access to the wireless traffic itself, thus averting any higher layer attack. Encompassing a number of key technologies spanning secure beamforming, artificial noise design, network coding, cooperative jamming, graph theory, and directional modulation, PS is now commonly accepted as one of the most effective forms of security.
While appealing as a theoretical concept, PS still faces a number of critical challenges that prevent it from wide commercial adoption in 5G and beyond, involving the lack of secure 5G signalling, the provision of eavesdroppers' information, and the applicability of existing theoretical techniques in real environments and under low-specification hardware.
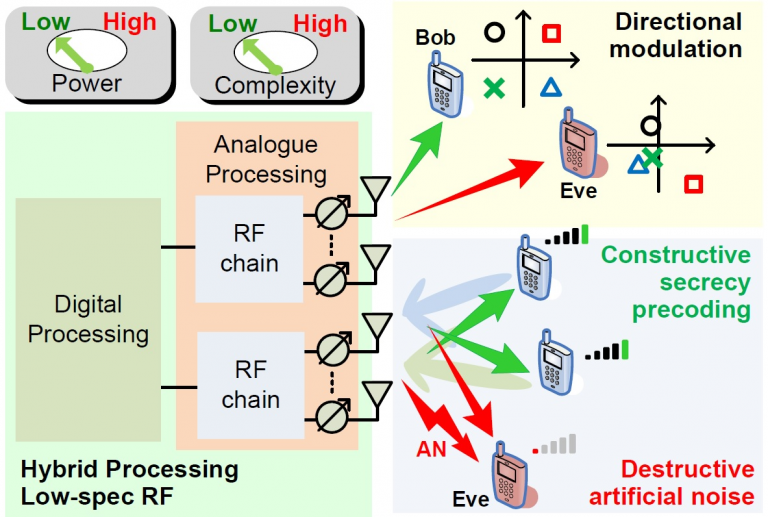
CI-PHY addresses the abovementioned challenges and promotes a paradigm shift on security by exploiting interference. In r, CI-PHY exploits constructive interference for Physical Layer Security by:
- Specifically tailored fundamental waveform design to exploit interference, that provides a low complexity solution with limited hardware requirements;
- Artificial noise and jamming to actively improve the desired receivers' SNR under secrecy constraints, and further improve secrecy by designing the artificial noise to align destructively to the signal at the eavesdropper;
- Robust approaches for real implementation by taking hardware impairments into account to reduce the hardware requirements for providing secrecy with resource-constrained devices;
- Real implementation and over-the-air testing of security solutions to evaluate and optimise performance in commercially relevant environments.
CI-PHY will be performed with the Interdisciplinary Centre for Security, Reliability and Trust in University of Luxembourg, and industrial partners QinetiQ, BT, National Instruments and Huawei, and aspires to kick-start an innovative ecosystem for high-impact players among the infrastructure and service providers of ICT to develop and commercialize a new generation of secure and power-efficient communication networks, and address the unprecedented vulnerability of emerging ICT services to cyber threats.
Outputs
- Publications
- M. R. Khandaker, C. Masouros, K. K. Wong, “Constructive Interference Based Secure Precoding: A New Dimension in Physical Layer Security”, IEEE Trans Forensics and Security., vol. 13, no. 9, pp. 2256-2268, Sept. 2018,
- M. R. Khandaker, C. Masouros, K. K. Wong, S. Timotheou, “Secure SWIPT by Exploiting Constructive Interference and Artificial Noise”, IEEE Trans. Comms., in press
 Close
Close

